Overview
Latest News: Updated the SSKR page with better description of SSKR Envelope including test vectors (2/12/25). Published Envelope Teaser video (8/21/24). Released GSTP, GSTP Tech Overview, and ESC pages (8/20/24). Released Undestanding Envelope, Understanding Envelope Extensions, and Understanding GSTP videos (8/13/24).
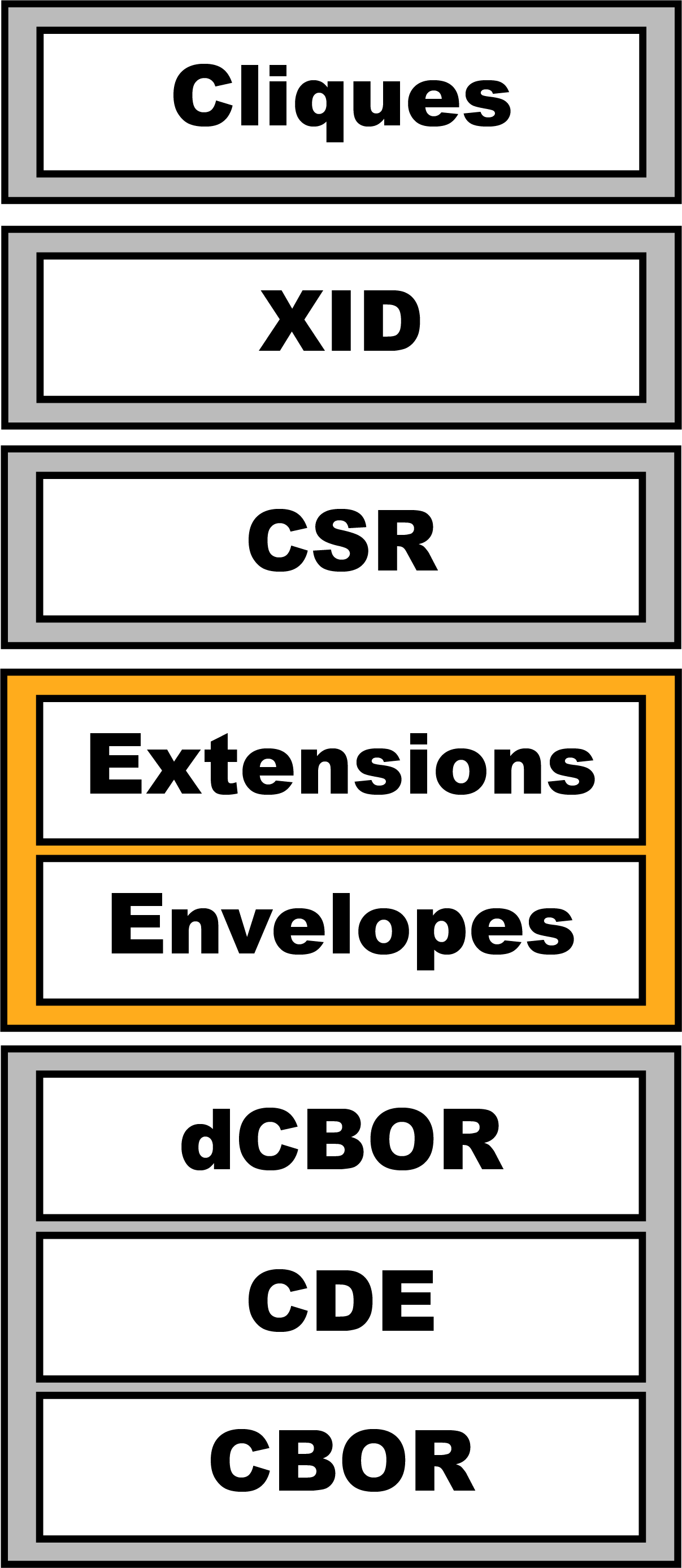
Gordian Envelope is a specification for the achitecture of a “smart document”. It builds on the binary format of the IETF CBOR standard to support the secure, reliable, and deterministic storage and transmission of data such as seeds, keys, decentralized identifiers, and verifiable credentials in a way that enables privacy while preserving structure. The format is very simple and compact, with minimal overhead, but thanks to its recursive design, documents can ultimately be as complex as needed. Gordian Envelope’s privacy features are built on a Merkle-like Tree that supports cryptography and privacy-related methodologies such as progressive trust and Merkle-based selective disclosure.
Blockchain Commons is currently working with multiple companies on the development and deployment of Gordian Envelope via regular monthly meetings; subscribe to our announcements-only mailing list or join our Signal channel if you’d like to get involved. You can also contact us if you’d prefer to get more information first.
Gordian Envelope is also on the experimental track as an Informational Draft for the IETF. Further, ongoing discussions are occurring with the W3C Credentials Community Group.
The Envelope as Metaphor
The name “envelope” was chosen for this smart-document architecture because that provides an excellent metaphor for its capabilities.


These capabilities include:
- Envelopes can have things written on them. Plaintext parts of a Gordian Envelope can be read by anyone.
- Envelopes can have routing instructions. That plaintext information can include data on how to use the Gordian Envelope, such as how to open or close it.
- Envelopes can contain things. Things can be placed within the structure of a Gordian Envelope.
- Envelopes can contain envelopes. The Gordian Envelope structure is fully recursive: any part of an envelope can actually be another envelope.
- Envelopes can have a seal. A signature can be made for the contents of an envelope, verifying their authenticity and that they haven’t been changed.
- Envelopes can be certified. Beyond just guarding against changes, a Gordian Envelope signature can also act as a certification of the envelope’s contents by some authority.
- Envelopes can be closed. Encryption allows any part of a Gordian Envelope to be protected from prying eyes.
- Envelopes can have windows. Selective disclosure allows for some parts of a Gordian Envelope to be readable while others have been redacted. Merkle proofs can proof that those parts were present in the original envelope.
- Different recipients can open envelopes in different ways. Just as people might use letter openers, their fingers, or a machine to open a normal envelope, special permits can grant people different ways to open a Gordian Envelope.
Why Is Gordian Envelope Important?
Gordian Envelope is intended as a more privacy-focused encoding architecture than existing data formats such as JWT and JSON-LD. We believe it has a better security architecture than JWT and that it doesn’t fall victim to the barriers of canonicalization complexity found in JSON-LD — which should together permit better security reviews of the Gordian Envelope design.
However, new features of Gordian Envelope not available in JWT or JSON-LD offer some of the best arguments for using the Smart Document structure.
- For a more extensive overview of Gordian Envelope, see Executive Summary.
- For a list of Gordian Envelope features, see Features List.
- For a technical look at Gordian Envelope, see Technical Overview.
Envelope Videos
|
Envelope Teaser:
|
Understanding Envelope I:
|
Understanding Envelope II:
|
See the Gordian Envelope playlist for more.
Libraries
Envelope Libraries
| Language | Repo | Contributor | Status |
|---|---|---|---|
| Rust | bc-envelope-rust | Blockchain Commons | |
| Swift | BCSwiftEnvelope | Blockchain Commons |
dCBOR Libraries
| Language | Repo | Contributor | Status |
|---|---|---|---|
| Ruby | cbor-dcbor gem | @cabo | |
| Rust | bc-dcbor-rust | Blockchain Commons | |
| Swift | BCSwiftDCBOR | Blockchain Commons | |
| TypeScript | bc-dcbor-ts | Blockchain Commons |
Envelope Links
Intro:
- Executive Summary
- Technical Overview
- Feature List
- IETF Problem Statement: Deterministic Hashed Data Elision (IETF)
Industry Intros:
- The Dangers of Digital Credentials in Education (blog article)
- Protecting Your Wellness Data with Hashed Elision (blog article)
Developer Resources:
- Envelope Technical Documents (GitHub repo)
- IETF Draft: The Envelope Structured Data Format (Editor’s Draft)
- dCBOR: Deterministic CBOR
Developer Extension Resources:
- BCR-2023-006: Attachment (GitHub repo)
- BCR-2023-005: Compression (GitHub repo)
- BCR-2023-009: Cryptographic Seeds (GitHub repo)
- BCR-2023-013: Cryptography (GitHub repo)
- BCR-2023-012: Expressions (GitHub repo)
- BCR-2024-006: Graphs (GitHub repo)
- BCR-2023-003: Known Values (GitHub repo)
- BCR-2023-003: Known Values (GitHub repo)
- BCR-2024-004: Transport Protocol (GitHub repo)
- BCR-2023-014: Sealed Transport Protocol (GitHub repo)
- BCR-2023-004: Symmetric Encryption (GitHub repo)
Developer Reference Apps:
- bc-envelope-cli-rust
- envelope-cli-swift (CLI implementation)
Specs & Research Papers:
- I-D: The Gordian Envelope Structured Data Format (IETF Draft)
- BCR-2023-003: Known Values (GitHub repo)
- BCR-2023-004: Symmetric Encryption (GitHub repo)
- BCR-2023-005: Compression (GitHub repo)
- BCR-2023-006: Attachments (GitHub repo)
- BCR-2023-009: Cryptographic Seeds (GitHub repo)
- BCR-2023-010: Bitcoin Output Descriptors (v3) (GitHub repo)
- BCR-2023-012: Expressions (GitHub repo)
- BCR-2023-013: Cryptography (GitHub repo)
- BCR-2023-014: Gordian Sealed Transaction Protocol (GSTP) (GitHub repo)
- BCR-2024-006: Representing Graphs (GitHub repo)
- BCR-2024-007: Decorrelation (GitHub repo)
- BCR-2024-009: Signatures with Metadata
Use Cases:
- Overview of Envelope Use Cases
- Summary of Use Cases
- Educational Use Cases (GitHub repo)
- Wellness Use Cases (GitHub repo)
- Data Distribution Use Cases (GitHub repo)
- Asset Control Use Cases (GitHub repo)
- Software Release Use Cases (GitHub repo)