Overview
Traditionally, self-sovereign identity has focused on the Single Signature Paradigm: a unique private key is controlled by a unique individual (or entity), and that key is used to define the entity and to verify decision and commitments made by the entity. The cliques model instead recoqnizes identification as a relationship between two or more entities.
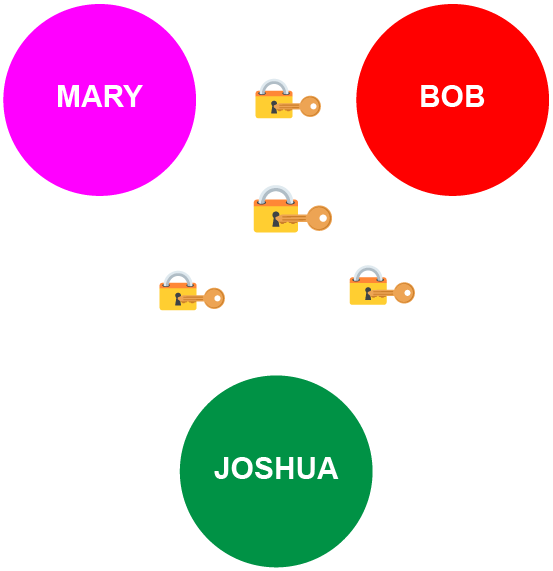
- Relational Edges are created between any two entities, with a private key jointly created using a Schnorr-based signature scheme, and with the corresponding public key identifying the edge. Decisions and commitments can then be made jointly by the two members, using the key.
- Cryptographic Cliques (or closed cliques) are created after forming relational edges between all members of a group. The relational edges then jointly create a key pair that represents the clique as a whole.
The following example demonstrates a three-person (triadic) clique:
Three variations of clique can increase their power:
- Open Cliques don’t require a connection between every member of the clique, allowing for organic evolution and expansion of a clique in a way that more closely matches the way that groups evolve.
- Fuzzy Cliques require the use of a threshold-based Schnorr signature scheme, such as FROST. They allow decisions and commitments to be made privately by subsets of a group.
- Device Cliques can include software or hardware elements such as oracles, wallets, fact checkers, and biometric verifiers. They can increase the power of cliques as the foundation for either groups or individuals.
The Musings articles, “Edge Identifiers & Cliques” and “Open & Fuzzy Cliques” give far more details on these foundational descriptions of cryptographic cliques.
|
Cliques Video:
|
Cliques Presentation:

|
Why Are Cliques Important?
Cliques recognize identification as a fundamentally relational activity. As such, they create the opportunity to model identity with a totally new eye, avoiding many of the pitfalls of traditional identity. Other advantages that are detailed in “Edge Identifiers & Cliques” include:
- Decentralized Identity Management
- Identity Validation
- Resilience Against Single Points of Failure
- Secure Group Decision Making
- Enhanced Privacy in Group Interactions
From the start, self-sovereign identity was intended to be about individuals interacting with a larger world. Some self-sovereign identity models have instead become too self-centric. Cliques offer a different way.
Links
Cliques:
- “Edge Identifiers & Cliques” (2024) (Musings)
- “Open & Fuzzy Cliques” (2024) (Musings)
Schnorr:
- “A Layperson’s Intro to Schnorr” (2023) (Musings)
Self-Sovereign Identity:
- “The Path to Self-Sovereign Identity” (2016) (Life with Alacrity)
- “Self-Sovereign Identity: Five Years On” (2021) (Musings)
- “The Origins of Self-Soveriegn Identity” (2023) (Musings)