These test vectors demonstrate SSKR test vectors for Blockchain Commons’ standard seeds. THey are broken into four categories:
WARNING. SSKR is non-deterministic. There is a random factor introduced when the shares are created, which means that every time you generate shares, they will be different. This is an expected and correct result. For the purposes of these test vectors, this means that if you generate SSKR shares from these seeds, they will be different. However, you can still test your implementation by reading these shares back in to make sure they reconstruct the expected seeds. LifeHash is an important tool for quickly recognizing a seed.
128-bit Seed
The example uses Blockchain Commons’ default 128-bit seed, YINMN BLUE.
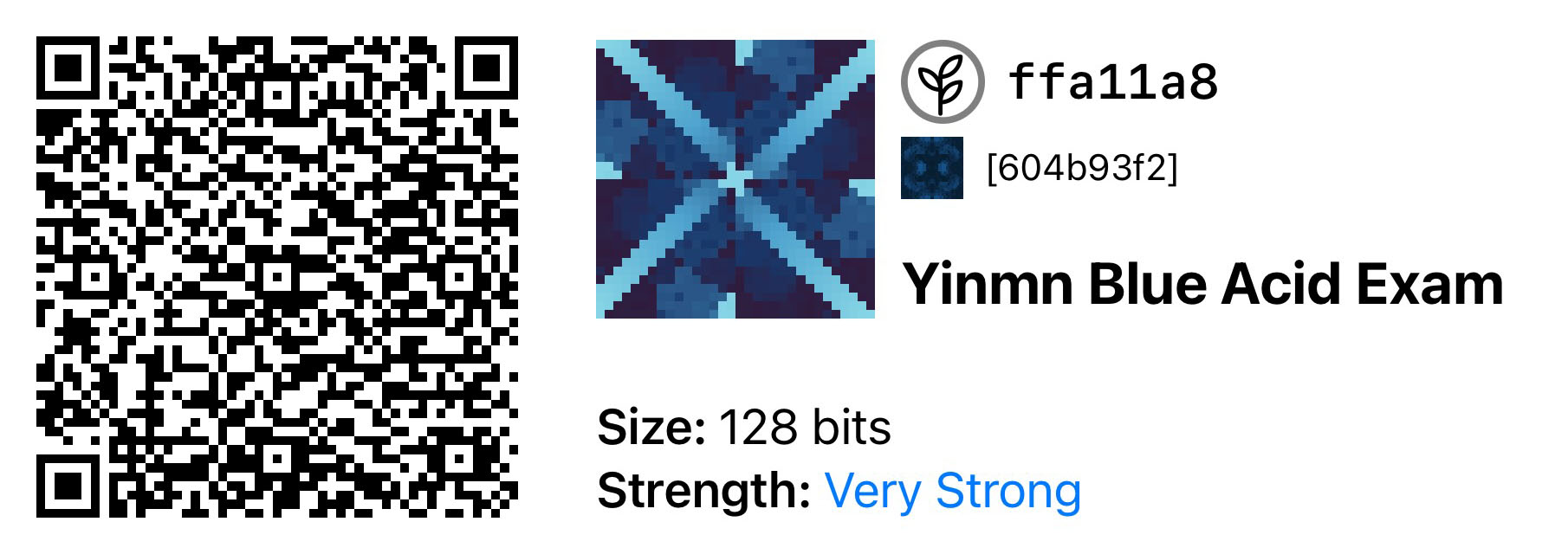
HEX: 59f2293a5bce7d4de59e71b4207ac5d2
BIP-39 WORDS: fly mule excess resource treat plunge nose soda reflect adult ramp planet
BYTEWORDS: hawk whiz diet fact help taco kiwi gift view noon jugs quiz crux kiln silk tied omit keno lung jade
GORDIAN ENVELOPE (with METADATA): ur:envelope/lptpsogdhkwzdtfthptokigtvwnnjsqzcxknsktdoybdtpsojyhkinjtjnjtcxfwjzkpihcxfpiainiecxfekshsjnoyadcsspoybetpsosecyidbbwnnnoyaatpsoksdighisinjkcxinjkcxjlkpjpcxjkjyhsjtiehsjpiecxeheyetdpidinjycxjyihjkjycxjkihihiedmplrnihld
SEGWIT UR OUTPUT DESCRIPTOR: ur:output-descriptor/oeadisktjojeisdefzdydtaolytantjloxaxhdclaxvlcprfttldjobkredtlnhsidwybaeyjtswyandlgjnehtkdsidbkqzsrkphyfhsaaahdcxhnfgnepefxgdytryckticelyotsstoknfntavevaskiddmolsarntykbrybtjpksamtantjooeadlncsghykaeykaeykaocyhngrmuwzaycyzssajpsndifmkohy
SEGWIT TEXT OUTPUT DESCRIPTOR: wpkh([604b93f2/84'/0'/0']xpub6DVfq9VduocgjGeR69Nyr8CCi9w5gywnU7wXMYGswpHjffjcbLYNzz6G6555VDcSZLDwZPzJHJQabVWWgkpvYntpunL3UjHGrkCJ6VndbQf)#ncwysjuk
![]() Do not use this seed to hold real monies; they could
disappear immediately!
Do not use this seed to hold real monies; they could
disappear immediately!
SSKR Envelope Test Vectors
The SSKR Envelope format is our current preference as a best practice because it allows the preservation of metadata and even the storage of multiple seedes or keys in a single container.
Two-of-Three SSKR
A traditional use of Shamir’s Secret Sharing shards a secret into three shares, and then allows the secret to be reconstructed from two of those shares.
The following set of 2-of-3 shares was generated by Gordian SeedTool and exported as Envelopes:
ur:envelope/lftansfwlrhdjzjnntonknktfwrehlfliycybasezebymuhklkbanthekkksuezoylhttncnstzeimtlwdstrnwsgulandhtbnasdlfecwieeymwbkkkaoaoimhpkplkwmwtzenyrhecrftkdaregrbbwdleenveetbbptfefsflehjlimpezeasbsbdcfghmdnsbshdtyjpfgfrmywzspaoyadndmlsglglbzgsbkwtdifdsktpjyptfxmwoywzgdasdwseveglhpvdiyglhpsrlyotbdjzimhddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaaxkeaeadaerpfzwmtlnnjzlubdbahhtkdnjztlbklaltknkbpsresbmupswlayaxptcmmuaocsztknemgu
ur:envelope/lftansfwlrhdjzjnntonknktfwrehlfliycybasezebymuhklkbanthekkksuezoylhttncnstzeimtlwdstrnwsgulandhtbnasdlfecwieeymwbkkkaoaoimhpkplkwmwtzenyrhecrftkdaregrbbwdleenveetbbptfefsflehjlimpezeasbsbdcfghmdnsbshdtyjpfgfrmywzspaoyadndmlsglglbzgsbkwtdifdsktpjyptfxmwoywzgdasdwseveglhpvdiyglhpsrlyotbdjzimhddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaaxkeaeadadimrkgwcksphtsbguwzrfenosoyhlzmbeonmoaosgkokesemyidurtkkggyrezctdndjyhpzc
ur:envelope/lftansfwlrhdjzjnntonknktfwrehlfliycybasezebymuhklkbanthekkksuezoylhttncnstzeimtlwdstrnwsgulandhtbnasdlfecwieeymwbkkkaoaoimhpkplkwmwtzenyrhecrftkdaregrbbwdleenveetbbptfefsflehjlimpezeasbsbdcfghmdnsbshdtyjpfgfrmywzspaoyadndmlsglglbzgsbkwtdifdsktpjyptfxmwoywzgdasdwseveglhpvdiyglhpsrlyotbdjzimhddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaaxkeaeadaobzpmrohdeyaebdrkweltdsdeweuezorksrpalnhndernemwdverylacmmkurvdmssawlbeke
Breaking Down the Test Vector: Using the envelope-cli on the first SSKR share simply shows that the Envelope contains an ENCRYPTED subject with its SSKR share being an assertion. T
% envelope format $SSKR_E
ENCRYPTED [
'sskrShare': SSKRShare
]
You can break down the CBOR encoded by the ur:envelope further by taking just the minimal Bytewords (everything after ur:envelope/) and converting them to hex using the bytewords-cli:
% bytewords -i minimal -o hex $SSKR_E_BW
82d99c4284586c6d9da57a7742b55d47661a0ec1fe1193598c0e9d5f7978defbf75ada23c7fe6ad5eac7beef53809b5a0c092f451b6432940a7902026a5b758cebf0fe9ab935bccf25b54b14ea8a36e43814a9453d47316f6aaffe090f0b1954959c0f58d472463b8ff2c802f82b2e834e4e154c0af02748c5d874a94394a1f250092cc1e44e5be7664e5bc381a30b6c6a5825d99c4158208d20803877b17c331c63dd78e08e284b096ddd038493d466d6dbec09a3ecc33da106d8c9d99d755825037c000100b640ebd59e6c8b0b0e5ccf2b6cd50a80877a7eacb5cb93ace90803a916930218
You can then look at the CBOR at cbor.me:
82 # array(2)
D9 9C42 # tag(40002)
84 # array(4)
58 6C # bytes(108)
6D9DA57A7742B55D47661A0EC1FE1193598C0E9D5F7978DEFBF75ADA23C7FE6AD5EAC7BEEF53809B5A0C092F451B6432940A7902026A5B758CEBF0FE9AB935BCCF25B54B14EA8A36E43814A9453D47316F6AAFFE090F0B1954959C0F58D472463B8FF2C802F82B2E834E4E15 # "m\x9D\xA5zwB\xB5]Gf\u001A\u000E\xC1\xFE\u0011\x93Y\x8C\u000E\x9D_yx\xDE\xFB\xF7Z\xDA#\xC7\xFEj\xD5\xEAǾ\xEFS\x80\x9BZ\f\t/E\ed2\x94\ny\u0002\u0002j[u\x8C\xEB\xF0\xFE\x9A\xB95\xBC\xCF%\xB5K\u0014\xEA\x8A6\xE48\u0014\xA9E=G1oj\xAF\xFE\t\u000F\v\u0019T\x95\x9C\u000FX\xD4rF;\x8F\xF2\xC8\u0002\xF8+.\x83NN\u0015"
4C # bytes(12)
0AF02748C5D874A94394A1F2 # "\n\xF0'H\xC5\xD8t\xA9C\x94\xA1\xF2"
50 # bytes(16)
092CC1E44E5BE7664E5BC381A30B6C6A # "\t,\xC1\xE4N[\xE7fN[Á\xA3\vlj"
58 25 # bytes(37)
D99C4158208D20803877B17C331C63DD78E08E284B096DDD038493D466D6DBEC09A3ECC33D # "ٜAX \x8D \x808w\xB1|3\u001Cc\xDDx\xE0\x8E(K\tm\xDD\u0003\x84\x93\xD4f\xD6\xDB\xEC\t\xA3\xEC\xC3="
A1 # map(1)
06 # unsigned(6)
D8 C9 # tag(201)
D9 9D75 # tag(40309)
58 25 # bytes(37)
037C000100B640EBD59E6C8B0B0E5CCF2B6CD50A80877A7EACB5CB93ACE90803A916930218 # "\u0003|\u0000\u0001\u0000\xB6@\xEB՞l\x8B\v\u000E\\\xCF+l\xD5\n\x80\x87z~\xAC\xB5˓\xAC\xE9\b\u0003\xA9\u0016\x93\u0002\u0018"
The encrypted subject is marked by tag 40002. It has four parts as described in BCR-2022-001. There is then a map of assertions on that subject, each of which is marked by the leaf tag 201. The one assertion on the subject is tagged 40309: it’s an SSKR share. (See the UR Registry for a listing of all Envelope-related tags.)
The envelope-cli also demonstrates that joining two different shares decrypts the SSKR Envelope, revealing not just a seed, but metadata (which is the advantage of using SSKR Envelope rather than SSKR UR):
% envelope sskr join $SSKR_E $SSKR_E_1 | envelope format
Bytes(16) [
'isA': 'Seed'
'date': 2022-02-22T14:22:22Z
'name': "Yinmn Blue Acid Exam"
'note': "This is our standard 128-bit test seed."
]
The Two-of-Three Two-of-Three SSKR
SSKR can support arbitrary groups, where you can then reconstruct a secret by using some number of shares from some number of groups.
One example is a two-of-three two-of-three (grouped four-of-nine) SSKR. Three groups are created, each of which has three shares. Reconstructing the secret requires a threshold of two shares from a threshold of two groups. In other words, the secret can be reconstructed from four of the nine shares, provided that they are two each from two of the groups.
The following set of two-of-three 2-of-3 shares was generated by Gordian SeedTool and exported as Envelopes.
Group 1:
ur:envelope/lftansfwlrhdjzdafwtbgaiycemutywzcpdmisgspttihljogrzmmkbdbwuotlctrpbzlnbkwnlnonnnssmwfmayvauogdztktbdryeoatfgvwfzkpuelfhlcsylketntnfduocwldhfpfhtnsolcnfztpfdlrynjzaoesfrcnmhjnfzhdlnhdjywnplfdherdaapkesayisidiaayzsinskrdlnhgtdmnjyuygssnndrhyldkksiyoxemiaidntgdcybtrsmybyjnbkimatjpzerkttahtehshddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaleimbgadaefrhdvtswktjkuewzatttgadlhpamyaosdrtiuetyhglgrkztkbmevdehmesnhdnlbgzogria
ur:envelope/lftansfwlrhdjzdafwtbgaiycemutywzcpdmisgspttihljogrzmmkbdbwuotlctrpbzlnbkwnlnonnnssmwfmayvauogdztktbdryeoatfgvwfzkpuelfhlcsylketntnfduocwldhfpfhtnsolcnfztpfdlrynjzaoesfrcnmhjnfzhdlnhdjywnplfdherdaapkesayisidiaayzsinskrdlnhgtdmnjyuygssnndrhyldkksiyoxemiaidntgdcybtrsmybyjnbkimatjpzerkttahtehshddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaleimbgadadhhtktighkggtftwplpgrfxflcsdahyihsscfrhhftdvthfdahkgrhhkprfhppywyaxvyieje
ur:envelope/lftansfwlrhdjzdafwtbgaiycemutywzcpdmisgspttihljogrzmmkbdbwuotlctrpbzlnbkwnlnonnnssmwfmayvauogdztktbdryeoatfgvwfzkpuelfhlcsylketntnfduocwldhfpfhtnsolcnfztpfdlrynjzaoesfrcnmhjnfzhdlnhdjywnplfdherdaapkesayisidiaayzsinskrdlnhgtdmnjyuygssnndrhyldkksiyoxemiaidntgdcybtrsmybyjnbkimatjpzerkttahtehshddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaleimbgadaoykjnlaytjlbsbttocszehlzmutfzpeetwehkbesbfghgkngodyfmlerhsbzsonktlpwzmhrf
Group 2:
ur:envelope/lftansfwlrhdjzdafwtbgaiycemutywzcpdmisgspttihljogrzmmkbdbwuotlctrpbzlnbkwnlnonnnssmwfmayvauogdztktbdryeoatfgvwfzkpuelfhlcsylketntnfduocwldhfpfhtnsolcnfztpfdlrynjzaoesfrcnmhjnfzhdlnhdjywnplfdherdaapkesayisidiaayzsinskrdlnhgtdmnjyuygssnndrhyldkksiyoxemiaidntgdcybtrsmybyjnbkimatjpzerkttahtehshddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaleimbgbyaehfmyamvaueoyrftlwycpbeospybwmdeowzdkuyctbwktaaaarpsncnatatdkjyzsjebsathg
ur:envelope/lftansfwlrhdjzdafwtbgaiycemutywzcpdmisgspttihljogrzmmkbdbwuotlctrpbzlnbkwnlnonnnssmwfmayvauogdztktbdryeoatfgvwfzkpuelfhlcsylketntnfduocwldhfpfhtnsolcnfztpfdlrynjzaoesfrcnmhjnfzhdlnhdjywnplfdherdaapkesayisidiaayzsinskrdlnhgtdmnjyuygssnndrhyldkksiyoxemiaidntgdcybtrsmybyjnbkimatjpzerkttahtehshddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaleimbgbyaddndmwkptghurenaozowpnyamyawfdyttlgutgeketachecskfxfrdsidolisjovdoefybwhe
ur:envelope/lftansfwlrhdjzdafwtbgaiycemutywzcpdmisgspttihljogrzmmkbdbwuotlctrpbzlnbkwnlnonnnssmwfmayvauogdztktbdryeoatfgvwfzkpuelfhlcsylketntnfduocwldhfpfhtnsolcnfztpfdlrynjzaoesfrcnmhjnfzhdlnhdjywnplfdherdaapkesayisidiaayzsinskrdlnhgtdmnjyuygssnndrhyldkksiyoxemiaidntgdcybtrsmybyjnbkimatjpzerkttahtehshddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaleimbgbyaopstbytkstthlqdhnssonctzebtspsswpbnsnvotansrliyntflftdtsnhyrfkertfxprwzcy
Group 3:
ur:envelope/lftansfwlrhdjzdafwtbgaiycemutywzcpdmisgspttihljogrzmmkbdbwuotlctrpbzlnbkwnlnonnnssmwfmayvauogdztktbdryeoatfgvwfzkpuelfhlcsylketntnfduocwldhfpfhtnsolcnfztpfdlrynjzaoesfrcnmhjnfzhdlnhdjywnplfdherdaapkesayisidiaayzsinskrdlnhgtdmnjyuygssnndrhyldkksiyoxemiaidntgdcybtrsmybyjnbkimatjpzerkttahtehshddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaleimbgclaezopkryzobarnaapmlrwedkaeimhlcxzefhoyjlzmksdlsesrfraochiohkbzptndkgnydrrt
ur:envelope/lftansfwlrhdjzdafwtbgaiycemutywzcpdmisgspttihljogrzmmkbdbwuotlctrpbzlnbkwnlnonnnssmwfmayvauogdztktbdryeoatfgvwfzkpuelfhlcsylketntnfduocwldhfpfhtnsolcnfztpfdlrynjzaoesfrcnmhjnfzhdlnhdjywnplfdherdaapkesayisidiaayzsinskrdlnhgtdmnjyuygssnndrhyldkksiyoxemiaidntgdcybtrsmybyjnbkimatjpzerkttahtehshddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaleimbgcladpyfyfdjkiabsgwzcpkaenlfnbgsprofdqzprtksrcsmdvtfwspwlaxtkkowmkeluktftpaec
ur:envelope/lftansfwlrhdjzdafwtbgaiycemutywzcpdmisgspttihljogrzmmkbdbwuotlctrpbzlnbkwnlnonnnssmwfmayvauogdztktbdryeoatfgvwfzkpuelfhlcsylketntnfduocwldhfpfhtnsolcnfztpfdlrynjzaoesfrcnmhjnfzhdlnhdjywnplfdherdaapkesayisidiaayzsinskrdlnhgtdmnjyuygssnndrhyldkksiyoxemiaidntgdcybtrsmybyjnbkimatjpzerkttahtehshddatansfphdcxlgcxlaetktpakeeoceiautksvtmndegrasjnutaxlrmutyiytbuywpasotwpsrfsoyamtpsotantkphddaleimbgclaohpjngswttystmobttpdwfeksnyjzbdldeylteeltrofzlstnswtkfhdwatwzcsrkatingdnl
SSKR UR Test Vectors
The ur:sskr format has generally been deprecated. An SSKR Envelope that locks data, including seeds, with an SSKRed symmetric key is now the preferred methodology.
Nonetheless, the following test vectors are presented in case of the need for a simple ur:sskr, for example in a more constrained environment.
Two-of-Three SSKR
The following set of 2-of-3 shares were exported as SSKR URs from Gordian Seed Tool.
ur:sskr/goayhsaeadaelosbmnpmhpwprtktctdsjlzspdhksepkcshglgrp
ur:sskr/goayhsaeadadlkfpyknbhpkkrotajpeycebwsgtipakitaskhdki
ur:sskr/goayhsaeadaolassksrlhputdydyskbaldeojzgdclctwmehkkwy
As explained in the Uniform Resource (UR) specification, URs are built from a minimal (two-character) version of ByteWords. Where URs self identify with their prefix (ur:sskr), Bytewords instead self identify with a ByteWords prefix (tuna next keep) that is a ByteWords encoding of the CBOR tag.
tuna next keep gyro away huts able acid able logo stub main poem help wasp rust kept cost days jowl zaps paid hawk safe peck bald pose diet keno
tuna next keep gyro away huts able acid acid luck flap yank numb help kick redo tuna jump easy code brew song taxi puma kiwi song figs zest ruby
tuna next keep gyro away huts able acid also lava sets keys real help unit duty duty silk beta loud echo jazz good curl cost yoga solo unit drum
Breaking Down the Test Vector: See the SSKR FAQ for a description of what the different parts of an SSKR share mean. As described there, the first share breaks down as following:
-
tuna next keep= SSKR (d99d75or CBOR tag#6.40309) -
gyro= length -
away huts= fingerprint for this sharding -
able acid= 2-of-3 -
able= share 1 -
logo stub main poem help wasp rust kept cost days jowl zaps paid hawk safe peck= share -
bald pose diet keno= checksum
The UR then uses the minimal ByteWords form, meaning that it
shows only the first and last letter of each word. This means that
“go” is “gyro”, “ay” is “away”, “hs” is “huts”, “ae” is “able”, “ad” is “acid”, etc. The ur: and ByteWords versions of the test vector therefore match precisely except for the characters at the front and the back.
- The UR self identifies with
ur:sskrprior to the length while the ByteWords self identifies withtuna next keep(CBOR #6.40309) prior to the length. - The last four digits are checksums and therefore are different in the two versions (
bald pose diet kenoversuscshglgrp) because of the prior difference.
256-bit Seed
The example uses Blockchain Commons’ default 256-bit seed, KHAKI.
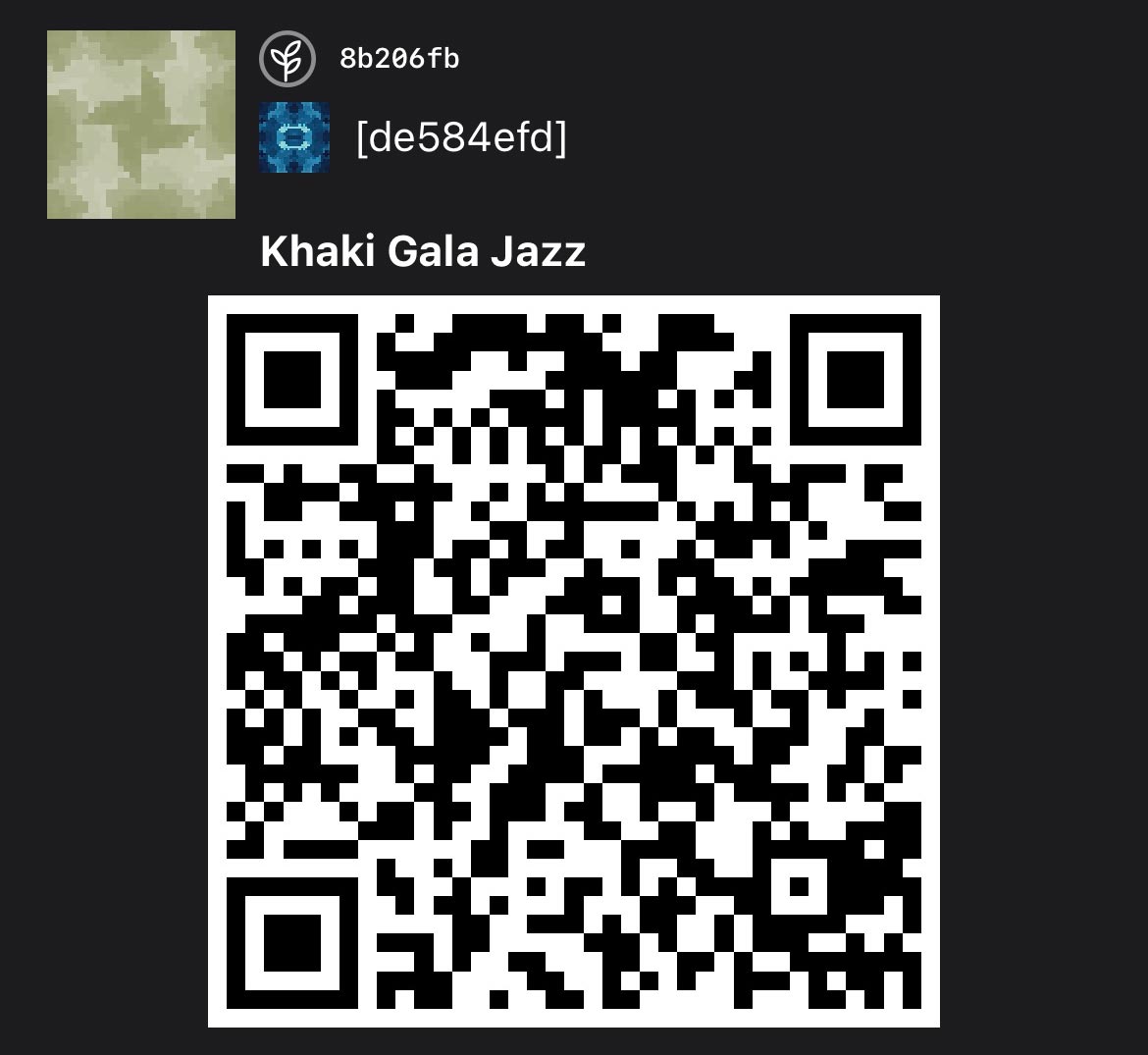
HEX: e3955cda304771c0031895637f55c3abe45153c87abd81c51ed14e8aafa1af13
BIP-39 WORDS: toe priority custom gauge jacket theme arrest bargain gloom wide ill fit eagle prepare capable fish limb cigar reform other priority speak rough imitate
BYTEWORDS: vial mild high twin duty fuel jugs rust apex cats mild idea lamb gyro scar play vibe gray guru soap kiln ruby lazy silk cook tent girl love pose obey pose brew exit gray king iced
GORDIAN ENVELOPE (with METADATA): ur:envelope/lptpsohdcxvlmdhhtndyfljsrtaxcsmdialbgosrpyvegyguspknrylyskckttgllepeoypebwoyadcsspoycfadzttpsotantjyoeadisktjojeisdefzdydtaolytantjloxaxhdclaodsjnasrfrtytvdcfvawyluladinygrgyjeesoekibtwdoecllafehgdezmpfrlfdaahdcxzttyeeetzmskiorkdntlwfrehytlhypajosrvthfcfplyklyjztdqzmemwgdotwlamtantjooeadlncsghykaeykaeykaocyuehdglzcaycyhdoytolnoybetpsosecyhhdnpafmoybdtpsoksdieyecendpidinjycxguihihiecxgdkpidjziniacxghihjkjycxhfihiajyjljpcxdegrishsjeindtsnlrfpjs
SEGWIT UR OUTPUT DESCRIPTOR: ur:output-descriptor/oeadisktjojeisdefzdydtaolytantjloxaxhdclaodsjnasrfrtytvdcfvawyluladinygrgyjeesoekibtwdoecllafehgdezmpfrlfdaahdcxzttyeeetzmskiorkdntlwfrehytlhypajosrvthfcfplyklyjztdqzmemwgdotwlamtantjooeadlncsghykaeykaeykaocyuehdglzcaycyhdoytolntdkezsfw
SEGWIT TEXT OUTPUT DESCRIPTOR: wpkh([de584efd/84'/0'/0']xpub6CJZ4hvDg49xgXpHh1h5MsKuxnpnu5m1shocnzueZUry1nrRjbAJhBPaDoByGSXKVyXJYdydRtiGps63oNP43hzbxHU9ey5mH3Cm6NNvSSo)#hxn88s0v
![]() Do not use this seed to hold real monies; they could
disappear immediately!
Do not use this seed to hold real monies; they could
disappear immediately!
SSKR Envelope Test Vectors
The SSKR Envelope format is our current preference as a best practice because it allows the preservation of metadata and even the storage of multiple seedes or keys in a single container.
Two-of-Three SSKR
A traditional use of Shamir’s Secret Sharing shards a secret into three shares, and then allows the secret to be reconstructed from two of those shares.
The following set of 2-of-3 shares was generated by Gordian SeedTool and exported as Envelopes:
ur:envelope/lftansfwlrhdurlrktkphyoygtcfuykpwmcxaogwihgdpdvlsnjnkbbsldgldmryghdlswuokpdlieknrelulnwetlgafmcmbestqdcprypsamtysatkfmrnfpjnaegadsfeflsflrnylkosdikbursshekgiyrfwpmyoslaryjpecluptdslrrsjtaeenetwppmidnthftitprlbelkckdwndwydilswzintndradoxioueaxftdsmyensorokgrhbnqzcluegtgrlsyamhdedrrdjytdfzhppmfzjsbwkiennykpnswfdwjnzsjzlfbydenlytiadmjlhhoymtluynswwkjtzmotchotwfdpmydwimvwpdutfymycmmukknesovabzwykoidcendpfswrsoysbiobadlswmssoescadphyflkkoslapkbsdsrndyptmtoemsosgskbfwnldttpsffrkgyatkdtnbgdhypsnywzweqzsezolkstsknyswtncnwmhddatansfphdcxkncsimjejnfmbgylwmlfykqzbsvtaomelatpbzsrinhygdwkjkgedrurfyvwhylkoyamtpsotantkphddaftfgaeadaedtmntdvtwlfpjkdsjymyfyryadwzptaajohkuobkfwjecsoxvlgodnvsjonblsesatzclazs
ur:envelope/lftansfwlrhdurlrktkphyoygtcfuykpwmcxaogwihgdpdvlsnjnkbbsldgldmryghdlswuokpdlieknrelulnwetlgafmcmbestqdcprypsamtysatkfmrnfpjnaegadsfeflsflrnylkosdikbursshekgiyrfwpmyoslaryjpecluptdslrrsjtaeenetwppmidnthftitprlbelkckdwndwydilswzintndradoxioueaxftdsmyensorokgrhbnqzcluegtgrlsyamhdedrrdjytdfzhppmfzjsbwkiennykpnswfdwjnzsjzlfbydenlytiadmjlhhoymtluynswwkjtzmotchotwfdpmydwimvwpdutfymycmmukknesovabzwykoidcendpfswrsoysbiobadlswmssoescadphyflkkoslapkbsdsrndyptmtoemsosgskbfwnldttpsffrkgyatkdtnbgdhypsnywzweqzsezolkstsknyswtncnwmhddatansfphdcxkncsimjejnfmbgylwmlfykqzbsvtaomelatpbzsrinhygdwkjkgedrurfyvwhylkoyamtpsotantkphddaftfgaeadaduomyrllflawtkgmhlamtvsdlvtssihatwdjpnetalgkgheuosrktrteymhvtidwpnsylghyt
ur:envelope/lftansfwlrhdurlrktkphyoygtcfuykpwmcxaogwihgdpdvlsnjnkbbsldgldmryghdlswuokpdlieknrelulnwetlgafmcmbestqdcprypsamtysatkfmrnfpjnaegadsfeflsflrnylkosdikbursshekgiyrfwpmyoslaryjpecluptdslrrsjtaeenetwppmidnthftitprlbelkckdwndwydilswzintndradoxioueaxftdsmyensorokgrhbnqzcluegtgrlsyamhdedrrdjytdfzhppmfzjsbwkiennykpnswfdwjnzsjzlfbydenlytiadmjlhhoymtluynswwkjtzmotchotwfdpmydwimvwpdutfymycmmukknesovabzwykoidcendpfswrsoysbiobadlswmssoescadphyflkkoslapkbsdsrndyptmtoemsosgskbfwnldttpsffrkgyatkdtnbgdhypsnywzweqzsezolkstsknyswtncnwmhddatansfphdcxkncsimjejnfmbgylwmlfykqzbsvtaomelatpbzsrinhygdwkjkgedrurfyvwhylkoyamtpsotantkphddaftfgaeadaotplkcsdkfretiagyltryatlftpnndraohebshtrlstgrmtghotbyvaflpycxhtloknimdmck
Breaking Down the Test Vector: Converting the minimal ByteWords of the UR to hex and decoding it at cbor.me reveals the following structure:
82 # array(2)
D9 9C42 # tag(40002)
84 # array(4)
58 DF # bytes(223)
8477755EA14D19DB75EB20024F6550A8E3CD6D7E0F894E2EBD542FC6DC752F647AB58B86EDD5493E1610C7B322BDAC06D4C2CF3EBE416D0049264547CC849A8CA7277EDFC45F7B66BCEC8FA780BD72358BA92684BF6E003638ECAD629D56D0D8B7108C1E2C9BEE2783F269DA2A01A467DE033A268F36C9B87BB90CB421DE4D4B83F890282ABA74D2405BAD4071137D369A759CF32C6DFA6C82112899F9632E6F5CA1968BF6C6F46EFFA317A3F32D8F2C6AE5A8DD448F1693799FC9E615EE76621C9BB0C6BFA1CB670E2FC697C9391D2D5E4779A780AA0F26BE30A996A297A7 # "\x84wu^\xA1M\u0019\xDBu\xEB \u0002OeP\xA8\xE3\xCDm~\u000F\x89N.\xBDT/\xC6\xDCu/dz\xB5\x8B\x86\xED\xD5I>\u0016\u0010dz\"\xBD\xAC\u0006\xD4\xC2\xCF>\xBEAm\u0000I&EḠ\x9A\x8C\xA7'~\xDF\xC4_{f\xBC쏧\x80\xBDr5\x8B\xA9&\x84\xBFn\u000068\xEC\xADb\x9DV\xD0ط\u0010\x8C\u001E,\x9B\xEE'\x83\xF2i\xDA*\u0001\xA4g\xDE\u0003:&\x8F6ɸ{\xB9\f\xB4!\xDEMK\x83\xF8\x90(*\xBAt\xD2@[\xAD@q\u0013}6\x9Au\x9C\xF3,m\xFAl\x82\u0011(\x99\xF9c.o\\\xA1\x96\x8B\xF6\xC6\xF4n\xFF\xA3\u0017\xA3\xF3-\x8F,j\xE5\xA8\xDDD\x8F\u0016\x93y\x9F\xC9\xE6\u0015\xEEvb\u001C\x9B\xB0ƿ\xA1\xCBg\u000E/Ɨ\xC99\u001D-^Gy\xA7\x80\xAA\u000F&\xBE0\xA9\x96\xA2\x97\xA7"
4C # bytes(12)
7E429929D8CC3B7BF8CF29A0 # "~B\x99)\xD8\xCC;{\xF8\xCF)\xA0"
50 # bytes(16)
5EAC9AF2EDB4C1FB8CC7C59AC6DA23EB # "^\xAC\x9A\xF2\xED\xB4\xC1\xFB\x8C\xC7Ś\xC6\xDA#\xEB"
58 25 # bytes(37)
D99C4158207A186A6B6D3E12F7EB82F5B40FE0029180D815C3695E50F4734A2ADF44E55E8C # "ٜAX z\u0018jkm>\u0012\xF7\xEB\x82\xF5\xB4\u000F\xE0\u0002\x91\x80\xD8\u0015\xC3i^P\xF4sJ*\xDFD\xE5^\x8C"
A1 # map(1)
06 # unsigned(6)
D8 C9 # tag(201)
D9 9D75 # tag(40309)
58 25 # bytes(37)
3A46000100298ED2E0E9417326748F44BD01F2A9047059DC0A426B18A4E3552BE870A08339 # ":F\u0000\u0001\u0000)\x8E\xD2\xE0\xE9As&t\x8FD\xBD\u0001\xF2\xA9\u0004pY\xDC\nBk\u0018\xA4\xE3U+\xE8p\xA0\x839"
That demonstrates an encrypted (40002) Gordian Envelope subject and one assertion that’s an SSKR share (40309). See the 128-bit 2-of-3 vector for a full explanation of how to get this CBOR and what it means.
The Two-of-Three Two-of-Three SSKR
SSKR can support arbitrary groups, where you can then reconstruct a secret by using some number of shares from some number of groups.
One example is a two-of-three two-of-three (grouped four-of-nine) SSKR. Three groups are created, each of which has three shares. Reconstructing the secret requires a threshold of two shares from a threshold of two groups. In other words, the secret can be reconstructed from four of the nine shares, provided that they are two each from two of the groups.
The following set of two-of-three 2-of-3 shares was generated by Gordian SeedTool and exported as Envelopes.
Group 1:
ur:envelope/lftansfwlrhdfpaonlyljpfhytsbgdnbdktobbntvlsspdylotssolpezeaxisrljkjybevlueonpefrltiygskpcwrslagawnwetivacktldmenrfckrkmylewtiomkeymuknfhnyaeldjsgsropatnprttenskmtlkpdmkwegdttyagswfpkpafhkemuwfckwfoegucegshddatansfphdcxynjsoyihecgmdpqdyakiosssoswfwdptrsjsluutlfdwaatlkkzeadkgctmulgmwoyamtpsotantkphddaonhpbgadaepkdncftscmcnhpahdipltyutwpeyglztwpisndvyiylbbgenmofyknrllywphfcfvydleolo
ur:envelope/lftansfwlrhdfpaonlyljpfhytsbgdnbdktobbntvlsspdylotssolpezeaxisrljkjybevlueonpefrltiygskpcwrslagawnwetivacktldmenrfckrkmylewtiomkeymuknfhnyaeldjsgsropatnprttenskmtlkpdmkwegdttyagswfpkpafhkemuwfckwfoegucegshddatansfphdcxynjsoyihecgmdpqdyakiosssoswfwdptrsjsluutlfdwaatlkkzeadkgctmulgmwoyamtpsotantkphddaonhpbgadadlagahfcptibddmwshykbwdglbeberprhcxjpmypebzgynlkkhkvacncklblkjsynjlfyaomw
ur:envelope/lftansfwlrhdfpaonlyljpfhytsbgdnbdktobbntvlsspdylotssolpezeaxisrljkjybevlueonpefrltiygskpcwrslagawnwetivacktldmenrfckrkmylewtiomkeymuknfhnyaeldjsgsropatnprttenskmtlkpdmkwegdttyagswfpkpafhkemuwfckwfoegucegshddatansfphdcxynjsoyihecgmdpqdyakiosssoswfwdptrsjsluutlfdwaatlkkzeadkgctmulgmwoyamtpsotantkphddaonhpbgadaozewsltdslyjkpasgtlbzpdvtbskoonkojlhhqdkilacnctpdctcwspzeiydwcsuocmmkleeh
Group 2:
ur:envelope/lftansfwlrhdfpaonlyljpfhytsbgdnbdktobbntvlsspdylotssolpezeaxisrljkjybevlueonpefrltiygskpcwrslagawnwetivacktldmenrfckrkmylewtiomkeymuknfhnyaeldjsgsropatnprttenskmtlkpdmkwegdttyagswfpkpafhkemuwfckwfoegucegshddatansfphdcxynjsoyihecgmdpqdyakiosssoswfwdptrsjsluutlfdwaatlkkzeadkgctmulgmwoyamtpsotantkphddaonhpbgbyaeemmorlcmyltdnemodpprisswoxvendeopdlgbgaahnbgfrndgevlvatihlfpspdeyntnkewp
ur:envelope/lftansfwlrhdfpaonlyljpfhytsbgdnbdktobbntvlsspdylotssolpezeaxisrljkjybevlueonpefrltiygskpcwrslagawnwetivacktldmenrfckrkmylewtiomkeymuknfhnyaeldjsgsropatnprttenskmtlkpdmkwegdttyagswfpkpafhkemuwfckwfoegucegshddatansfphdcxynjsoyihecgmdpqdyakiosssoswfwdptrsjsluutlfdwaatlkkzeadkgctmulgmwoyamtpsotantkphddaonhpbgbyadlazcwpwzlatydehhfhykpajnmhcykbwmndjzesdiiawezofgguvdsgjnfpheattkhefpjyae
ur:envelope/lftansfwlrhdfpaonlyljpfhytsbgdnbdktobbntvlsspdylotssolpezeaxisrljkjybevlueonpefrltiygskpcwrslagawnwetivacktldmenrfckrkmylewtiomkeymuknfhnyaeldjsgsropatnprttenskmtlkpdmkwegdttyagswfpkpafhkemuwfckwfoegucegshddatansfphdcxynjsoyihecgmdpqdyakiosssoswfwdptrsjsluutlfdwaatlkkzeadkgctmulgmwoyamtpsotantkphddaonhpbgbyaofwgsadskcfuewdbzasfnselusfaxgemktoghfyfwiyylnbftkswmrnpaihkigtzcurguuofy
Group 3:
ur:envelope/lftansfwlrhdfpaonlyljpfhytsbgdnbdktobbntvlsspdylotssolpezeaxisrljkjybevlueonpefrltiygskpcwrslagawnwetivacktldmenrfckrkmylewtiomkeymuknfhnyaeldjsgsropatnprttenskmtlkpdmkwegdttyagswfpkpafhkemuwfckwfoegucegshddatansfphdcxynjsoyihecgmdpqdyakiosssoswfwdptrsjsluutlfdwaatlkkzeadkgctmulgmwoyamtpsotantkphddaonhpbgclaelepdietaiatngmwfplwpctjzhdrodlbkbnwfselscxfhsreoeynehfeycscwheidprvolngy
ur:envelope/lftansfwlrhdfpaonlyljpfhytsbgdnbdktobbntvlsspdylotssolpezeaxisrljkjybevlueonpefrltiygskpcwrslagawnwetivacktldmenrfckrkmylewtiomkeymuknfhnyaeldjsgsropatnprttenskmtlkpdmkwegdttyagswfpkpafhkemuwfckwfoegucegshddatansfphdcxynjsoyihecgmdpqdyakiosssoswfwdptrsjsluutlfdwaatlkkzeadkgctmulgmwoyamtpsotantkphddaonhpbgcladntiypmaxiaplesrptyvafrhkwzsrykkidtntbzstdrdtksjplffzgyenmsfrrprdrevdghpl
ur:envelope/lftansfwlrhdfpaonlyljpfhytsbgdnbdktobbntvlsspdylotssolpezeaxisrljkjybevlueonpefrltiygskpcwrslagawnwetivacktldmenrfckrkmylewtiomkeymuknfhnyaeldjsgsropatnprttenskmtlkpdmkwegdttyagswfpkpafhkemuwfckwfoegucegshddatansfphdcxynjsoyihecgmdpqdyakiosssoswfwdptrsjsluutlfdwaatlkkzeadkgctmulgmwoyamtpsotantkphddaonhpbgclaooxdlwekoiaeylrkkhtyahgamchgllavefgdljpbdeebwplpagafthdftcahpmtsolbkpiaut
SSKR UR Test Vectors
The ur:sskr format has generally been deprecated. An SSKR Envelope that locks data, including seeds, with an SSKRed symmetric key is now the preferred methodology.
Nonetheless, the following test vectors are presented in case of the need for a simple ur:sskr, for example in a more constrained environment.
Two-of-Three SSKR
The following set of 2-of-3 shares were exported as SSKR URs from Gordian Seed Tool.
ur:sskr/hddahgsoaeadaenbksihdtcavdcetdsbiamuwnjokgrehtfxpfvwbefgvwhnolaxbtjofxotaylnhycelukbgw
ur:sskr/hddahgsoaeadadsknywsrofnspkeehvsmhuymhsskbsgwfetsahkvsnbnebgjtghlpplkeeouytsmubzsabtcw
ur:sskr/hddahgsoaeadaoimosimbeherhuobslgnnaxeoaxjsgrbwreghlnzomebylrdppmamtsfsmkredkurjluttluy
As explained in the Uniform Resource (UR) specification, URs are built from a minimal (two-character) version of ByteWords. Where URs self identify with their prefix (ur:sskr), Bytewords instead self identify with a ByteWords prefix (tuna next keep) that is a ByteWords encoding of the CBOR tag.
tuna next keep hard data hang solo able acid able numb keys inch diet cola void code tied stub idea menu when judo king race heat flux puff view blue frog view horn oval apex belt judo flux omit away lion holy yurt echo yank kiln
tuna next keep hard data hang solo able acid acid silk navy webs redo fern soap kite each vows math ugly math sets knob song wolf exit saga hawk vows numb note brag jolt gush limp pool kite echo ugly toys menu what kiln lion drum
tuna next keep hard data hang solo able acid also item owls item blue hope rich undo bias lung noon apex echo apex jugs gear brew race gush lion zero maze body liar drop poem atom toys figs monk race dark user love inch holy waxy
Breaking Down the Test Vector: See the SSKR FAQ for a description of what the different parts of an SSKR share mean. As described there, the first share breaks down as following:
-
tuna next keep= SSKR (d99d75or CBOR tag#6.40309) -
hard data= length -
hang solo= fingerprint for this sharding -
able acid= 2-of-3 -
able= share 1 -
numb keys inch diet cola void code tied stub idea menu when judo king race heat flux puff view blue frog view horn oval apex belt judo flux omit away lion holy= share -
yurt echo yank kiln= checksum
The UR then uses the minimal ByteWords form, meaning that it shows only the first and last letter of each word. See the 256-bit 2-of-3 vector for a full explanation of how ByteWords and UR formats interrelate
Final Notes
SSKR is a powerful way to back up digital secrets. This example demonstrates two specific seeds and how they can be used to generate SSKR shares using two different groupings, either in the current SSKR Envelope format or the legacy SSKR UR format.